Cyber Security, in the current landscape of technology, it is crucial to recognize the significance of safeguarding against cyber threats. In today’s interconnected world, safeguarding sensitive information and systems from malicious attacks has become more crucial than ever before. This article seeks to simplify the complex world of cyber security, offering a thorough examination of its fundamental principles, effective protection strategies, and recommended approaches for both individuals and organizations. With a grasp of these fundamentals, we can all play a part in creating a more secure online environment.
Introduction to Cyber Security
Protecting computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks is of utmost importance. It covers a variety of methods and resources aimed at safeguarding the reliability, secrecy, and accessibility of information. Given the ever-increasing complexity and sophistication of cyber threats, it is imperative for individuals of all backgrounds to grasp the fundamentals of cyber security. This knowledge is particularly vital for those working in the field of information technology.
Key Concepts and Terminology
- Malware is a type of software that is intentionally created to cause harm or exploit programmable devices, services, or networks.
- Phishing is a sneaky strategy employed to trick people into revealing sensitive information by pretending to be a reliable source in online communication.
- Ransomware is a malicious software that poses a serious threat to the victim’s data. It can either block access to the data indefinitely or expose it to the public unless a ransom is paid.
- Firewall: A network security system that monitors and controls incoming and outgoing network traffic based on predefined security rules.

Understanding Cyber Threats
There are a wide range of cyber threats that can pose risks to digital and network infrastructure. Gaining knowledge about these risks is the initial stride towards ensuring strong security measures.
Read also: Google wants to remove AI spam contents from Google search results
Common Types of Cyber Attacks
- DDoS Attacks: Distributed Denial of Service attacks can overwhelm a system’s resources, making it inaccessible to intended users.
- Man-in-the-Middle (MitM) Attacks: This happens when malicious individuals intercept and modify communications between two parties without their awareness.
- SQL Injection: A malicious technique where code is inserted into SQL queries to manipulate databases and gain unauthorized access to sensitive information.

Cyber Security Best Practices
Ensuring the security of your digital environment requires the implementation of best practices. Here are some essential strategies that individuals and organizations should adopt:
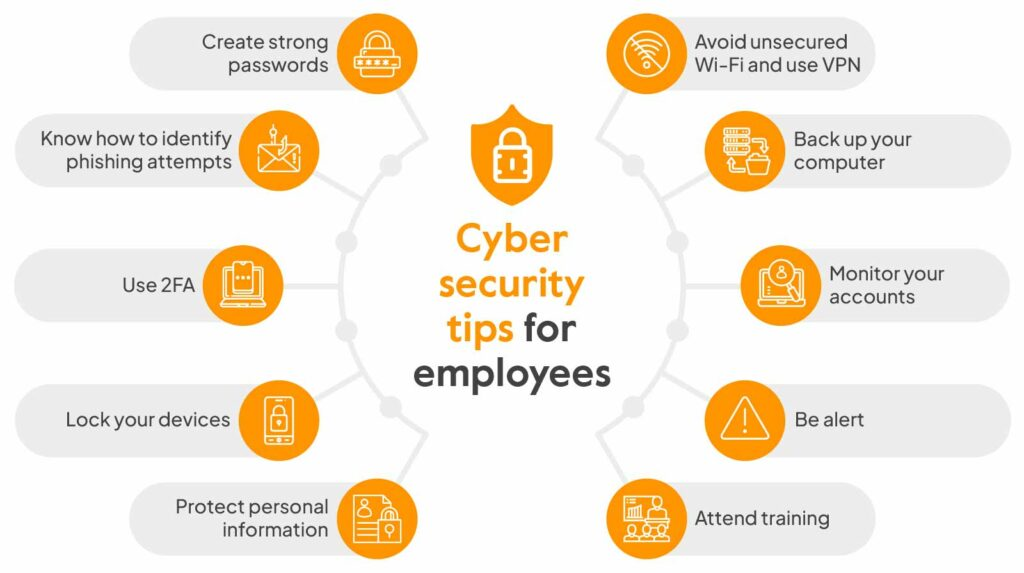
For Individuals
- Use Strong Passwords: Combine letters, numbers, and symbols to create complex passwords, and use a password manager to keep track of them.
- Regular Software Updates: Keep your operating system, applications, and any other software up to date to protect against vulnerabilities.
- Be Wary of Phishing Attempts: Always verify the authenticity of emails or messages that request personal information.
For Organizations
- Implement Access Control: Limit access to sensitive information and systems to authorized personnel only.
- Conduct Regular Security Assessments: Regularly evaluate your security posture to identify and mitigate potential vulnerabilities.
- Employee Training: Educate employees about cyber threats and safe online practices to prevent inadvertent breaches.
Advanced Cyber Security Measures
For individuals seeking to enhance their defenses against cyber threats, implementing advanced security measures can offer an extra level of protection.
Encryption
Securing data through encryption guarantees that intercepted information remains inaccessible and incomprehensible without the appropriate decryption key.
Intrusion Detection Systems (IDS)
These systems diligently keep an eye on network traffic, always on the lookout for any signs of suspicious activity. If any potential threats are detected, administrators are promptly notified to take necessary action.

Cyber Security and the Future
With the rapid advancement of technology, the ever-changing world of cyber threats is also evolving. Keeping up-to-date on the latest security trends and threats is crucial for maintaining strong defenses. It is anticipated that the field of cyber security will witness an increased utilization of artificial intelligence and machine learning technologies in order to proactively anticipate and thwart potential attacks.
Frequently Asked Questions (FAQs)
What are some effective strategies for safeguarding against cyber attacks?
It is crucial to adopt a comprehensive security strategy that includes various layers of protection, such as robust passwords, frequent software updates, thorough employee training, and cutting-edge security measures. This approach is proven to be highly effective in safeguarding against cyber threats.
Is antivirus software capable of providing comprehensive protection against all types of malware?
Although antivirus software is an essential part of safeguarding against cyber threats, it may not be able to provide complete protection against all types of malware, particularly advanced or emerging attacks. Regular updates and a well-rounded security strategy are essential.
What is the recommended frequency for updating passwords?
It is advisable to regularly update your passwords, ideally every three to six months. If you have any suspicions of a security breach, it is crucial to update your passwords immediately.
Is the responsibility for cyber security limited to IT departments?
Absolutely, ensuring cyber security is a collective effort. It is crucial for individuals and organizations to prioritize the protection of their information.
By understanding and implementing these fundamental principles of online security, we can collectively work towards establishing a more secure digital landscape. As we continue to navigate the intricacies of the digital age, it is crucial that we stay alert, well-informed, and proactive in our approach to safeguarding our online presence.